Information Security Awareness

Stephanie (Charlie) Farley – Open Education Resource Advisor for EDE  Last week was Information Security Awareness Week at The University of Edinburgh. At the main event for the week ‘Treat it like Treasure’ we heard from three speakers working in information security present their own perspective on day to day information security threats and how to combat them.
Last week was Information Security Awareness Week at The University of Edinburgh. At the main event for the week ‘Treat it like Treasure’ we heard from three speakers working in information security present their own perspective on day to day information security threats and how to combat them.
Dr Kami Vaniea (Lecturer in Cyber Security and Privacy)
Dr Vaniea started her presentation with a cyber security pop-quiz:
Question 1: Where does the link http://facebook.mobile.com take you?
A) Like postal addresses links are read right to left. The above link goes to a mobile.com webpage, not a facebook.com webpage.
Question 2: Does google know what you have typed before you click enter? 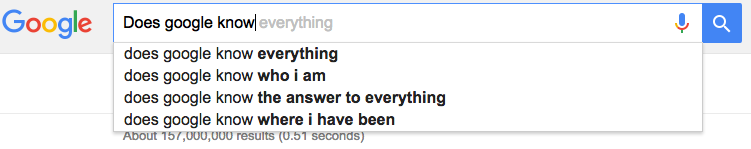 A) Yes. Google send the letters you type to their server for processing. The server then figures out what you are likely looking for and sends it back to make this list. Facebook has studies on all the things people decide NOT to post.
A) Yes. Google send the letters you type to their server for processing. The server then figures out what you are likely looking for and sends it back to make this list. Facebook has studies on all the things people decide NOT to post.
Question 3: Can we trust that the ‘from’ information provided in an email is trustworthy?
A) No. Links and URLs can be deceptive, the actual URL is the only one generated by the local computer and not the attacker. A good way to check is to mouse over (but don’t click) any link in an email, you should see a pop-up that shows the actual URL that the link points to, if the link doesn’t match, or if it’s a short link that doesn’t look right, then don’t click on it. 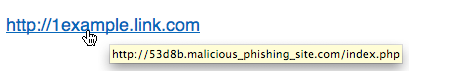
Kami emphasised that there is a very common misconception that opening web pages, emails, PDFs, and documents is like reading physical paper. But the act of visiting that webpage, opening that email, PDF or document is an action that causes code to run and that code can include malware.
The best predictor for being compromised (assuming you are doing the basics, like running an anti-virus, and updating regularly) is simply the number of website you visit. The more webpages you visit, the higher the odds that you will become the next compromised computer. Do you know how many websites you visit? Do you actually know if the websites you are visiting are ‘shady’? Even reputable websites can be at risk. Web pages are built dynamically out of many other websites and adds on reputable websites can be the delivery method of virus. Yahoo.com was hit by a malware attack in 2014 which was able to infect an estimated 27,000 individuals every hour.
Rafe Pilling (Senior Threat Researcher, SecureWorks)
Specialising in Counter Threat Work, Rafe and his team collect lots of data from lots of different sources and bring it together to analyse and actively monitor the cyber landscape for emerging threats and vulnerabilities. What do they see?
- Financial crime, the theft of money or of data that can be sold.
- Theft of data
- Obstructions of services
- Destruction of data
Crime as a Service is a sophisticated agile market. Usually operating from territories outside the UK or EU. There are organisations or groups that specialise in different services to assist other criminals in accessing your information. SecureWorks partner with law enforcement to work towards taking down organisations. Successes have including taking down GameOverZeus, a peer-to-peer botnet used for banking fraud and distribution of ransomware (although they are still looking for the head of the organisation). Ransomware is computer malware that installs on your computer or device and locks it so you can’t access or use your own information. It then demands a ransom payment to decrypt the malware or else it will either: A) destroy your data, all of your photos, documents, work, gone. B) publish your private details in a public arena.
In 2016 SecureWorks have tracked an 81% increase in ransomware incidence response engagements, and a 108% increase in ransomware variants and families.
Detective Sergent Adrian Ure, Cybercrime Operations, Police Scotland
Significant differences in investigating cyber crime to other crime. Cyber crime is borderless, this presents significant challenges for the police including but not limited to jurisdiction issues on the location of the victim, the witnesses, and the perpetrator.
Most of us have heard of the Dark web, and while it does have legitimate uses in oppressed countries where it can provide freedom and access of information, it is also used by crime organisations, where anything can be sold or supplied. For example, Social Engineering is a technique used by criminals to gather private details which can then be sole on the Dark web for a variety of purposes from identify theft and fraud.
Detective Ure confirmed that it is hard to solve cyber crime, but the more information the police are provided with, the more likely they’ll be able to build a case and track crimes. He also urged everyone to secure home wi-fi the same way that you lock up when you’re out. An unsecured wi-fi could be used for illegal purposes that will lead back to you and en-up with police knocking down your door at 5am in the morning on a raid.
How do we protect ourselves?
All three speakers at the event agreed there are some very specific things we can all do to improve our safety and protect against cybercrime.
Passwords Select a strong passcode, this means not using a word, even one that is a combination of letters and numbers as it will be vulnerable to a dictionary attack. One of the passwords discovered by the Cybercrime unit for a hacked company was ‘p@ssword1’.
Your core email account is usually the most important. If someone can hack your primary email account, they can use password recovery from here to gain access to your other accounts. Don’t store credentials in browsers. These are very easy to hack and steal.
Use a password manager for less important things that you use rarely. LastPass, OnePassword, and KeePass are the most recommended.
If you have important things you use rarely, pick a strong password and write it down somewhere safe (this is ok).
Install an anti-virus scanner
Whether this is by using the anti-virus that comes with your device, buying one, or using a free anti-virus, ensure that you are using something to scan your device for risks.
Update your software
Update patches for your software often include fixes to vulnerabilities and preventative measure for new malware and threats. By keeping your software up to date you will be at far less risk.
Back-up your data
Main advice to protect against ransomware file encryption is to back-up, back-up, back-up.
Install Ad-blockers Ad-blockers reduce the amount of content loading when you visit a website. Adds are also a delivery vehicle for malware even via trusted websites.
Be Suspicious!
Of everything. The websites you go to. Emails you receive. Don’t accept LinkedIn or Facebook invites from someone you don’t know. It’s a credibility link, to build-up trust and to exploit you and your machine. Be suspicious every time you’re asked to download something, or give permissions.



