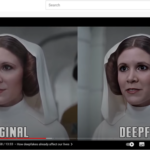
Big Brother: Is That Me or Deepfake?
Tom Cruise has gone viral. Is him playing golf in the video? Yes and No. It turns out to be a computer-generated figure just with Tom’s look. It is astonishingly real, isn’t it? We may regard Photoshop as an insane invention, but technology outperforms itself again. However, is this benignant or subversive?
Toxic
Risks:
-Fraud (wire fraud and Internet Fraud)
Altered images and videos can be identified by naked eyes or computer programs, but voices on the phone might be tricky.
Forbes: A Voice Deepfake Was Used To Scam A CEO Out Of $243,000
New Scientist: AI-generated deepfake voices can fool both humans and smart assistants
-Media Manipulation
The last thing you would want to see is the combination with political issues and deep-learning AI.
One risk is identity theft. Not necessarily to a legal extent. Sometimes not recognized by humans or algorithms
Mahmud and Sharmin (2021) :
"The another most malicious use of Deepfake is to exploit world leaders and politician by making fake videos of them and sometimes it could have been great risk for world peace."
van Dijck and Poell (2013):
"Social media platforms, like mass media, handle a variety of online systems for rating, polling, and surveying user responses; but beyond expressly triggered responses, platforms ostensibly have the capacity for polling built into their architecture. Facebook and Twitter increasingly wield their potential to mine online social traffic for indicators of trending topics, keywords, sentiments, public viewpoints, or frequently shared and liked items. Microblogging tool Twitter, more than any other platform, promotes itself as an echo chamber of people's opinions, even positioning itself as a replacement of offline opinion polls.
The idea that social media are neutral, unmediated spaces is an important assumption ingrained in many definitions of data flows. Part of social media's logic lies in the assertion that data are "raw" resources merely being "channelled" through online veins, allowing researchers to perform "opinion mining" or "sentiment analysis" . Twitter supposedly measures informal sentiments, feelings, or underbellies of "the people" at a stage when they are still in the process of becoming "official" public opinion."
-Fake social network accounts
Many SNS accounts may be fabricated for trolling and cyberbullying. Some fans are crazy, who may occupy the first lines of comment board and blindly praise the one they follow, and launch large-scale attacks towards anyone who disagrees.
Images of fake people can just be formed every time you reload the web page: https://thispersondoesnotexist.com/
The computer program to generate voice, images, and motion pictures are advancing nearly on a daily basis: Goodfellow GAN programme
Westerlund (2019):
"Deepfakes are hyper-realistic videos digitally manipulated to depict people saying and doing things that never happened. Deepfakes are created using AI, that is, Generative Adversarial Networks (GANs) that pit discriminative and generative algorithms against one another to fine-tune performance with every repetition."
-Ethical issues
Except the legal issues that may occur, unethical use of Deepfake has already happened.
Mahmud and Sharmin (2021):
"Most common use of Deepfake technology is to make pornography of well known actress"
Benefits:
-improve resolution of compromised visual documents
revolution in entertainment industry
Mahmud and Sharmin (2021):
"Advertising and business purposes too. Technologists now are using the Deepfake to make copy of famous artwork such as creating video of famous Monalisa artwork using the image."
Credit: Sumsub
https://www.youtube.com/watch?v=U_j5AaVi07A
-it is just fun.
Everytime
Check the source, be mindful of fake news
Westerlund (2019):
"Four ways to combat deepfakes:
1) legislation and regulation,
2) corporate policies and voluntary action,
3) education and training, and
4) anti-deepfake technology that includes deepfake detection, content authentication, and deepfake prevention."
References:
Gillespie, T. 2010. The politics of ‘platforms’. New Media & Society. 12(3), pp.347–364.
Güera, D. and Delp, E.J. 2018. Deepfake Video Detection Using Recurrent Neural Networks In: 2018 15th IEEE International Conference on Advanced Video and Signal Based Surveillance (AVSS)., pp.1–6.
Humphreys, A. and Grayson, K. 2008. The Intersecting Roles of Consumer and Producer: A Critical Perspective on Co-production, Co-creation and Prosumption: Intersecting Roles of Consumer and Producer. Sociology Compass. 2(3), pp.963–980.
Korshunov, P. and Marcel, S. 2019. Vulnerability assessment and detection of Deepfake videos In: 2019 International Conference on Biometrics (ICB)., pp.1–6.
Mahmud, B.U. and Sharmin, A. 2021. Deep Insights of Deepfake Technology : A Review. arXiv:2105.00192 [cs].
Ritzer, G. and Jurgenson, N. 2010. Production, Consumption, Prosumption: The nature of capitalism in the age of the digital ‘prosumer’. Journal of Consumer Culture. 10(1), pp.13–36.
van Dijck, J. and Poell, T. 2013. Understanding Social Media Logic [Online]. Rochester, NY: Social Science Research Network. [Accessed 3 December 2021]. Available from: https://papers.ssrn.com/abstract=2309065.
Westerlund, M. 2019. The Emergence of Deepfake Technology: A Review. Technology Innovation Management Review. 9(11), pp.39–52.